Planning a vacation this summer? A little tech prep can help ensure that your devices don’t let you down while you’re away. We have advice for what to bring, essential apps, and more.


Planning a vacation this summer? A little tech prep can help ensure that your devices don’t let you down while you’re away. We have advice for what to bring, essential apps, and more.

If you use Google Chrome or another Chromium browser instead of Safari, you can stay secure by following two simple rules regarding updates and extensions.

For better results when a team or family group needs to share 2FA codes to log in to a website, try to use an authentication app instead of SMS, or better yet, use a password manager that can both generate 2FA codes and share logins with a group.

Apple’s iCloud Keychain password manager keeps improving, and we now recommend it, especially for those not already using a third-party password manager. Here’s how to use iCloud Keychain to store and enter secure passwords.

We all accumulate “trusted devices” in our Apple, Google, and password manager accounts, but it’s important to remove devices you no longer use because they could be security risks.

To ensure phishers don’t forge email from your domain to use in their attacks on your organization and others, you must implement SPF, DKIM, and DMARC. We explain the basics, and we’re happy to help with the setup.
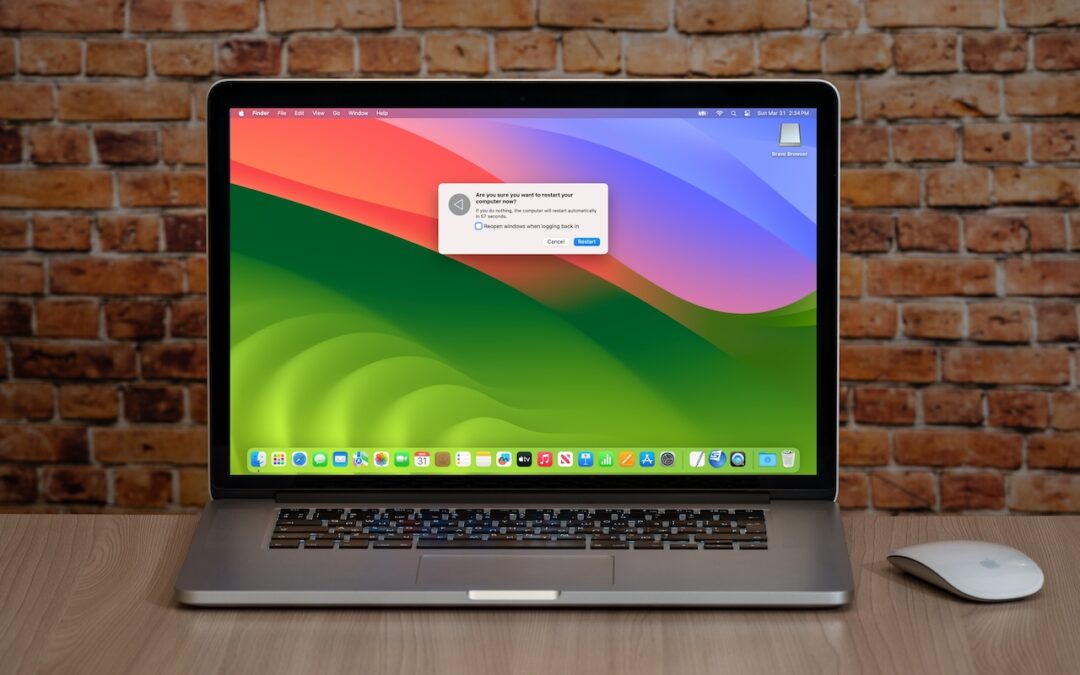
You can go for weeks or months without restarting your Mac, but it’s a good idea to restart more frequently to increase security, avoid or resolve problems, get updates, and generally clear your Mac’s decks.
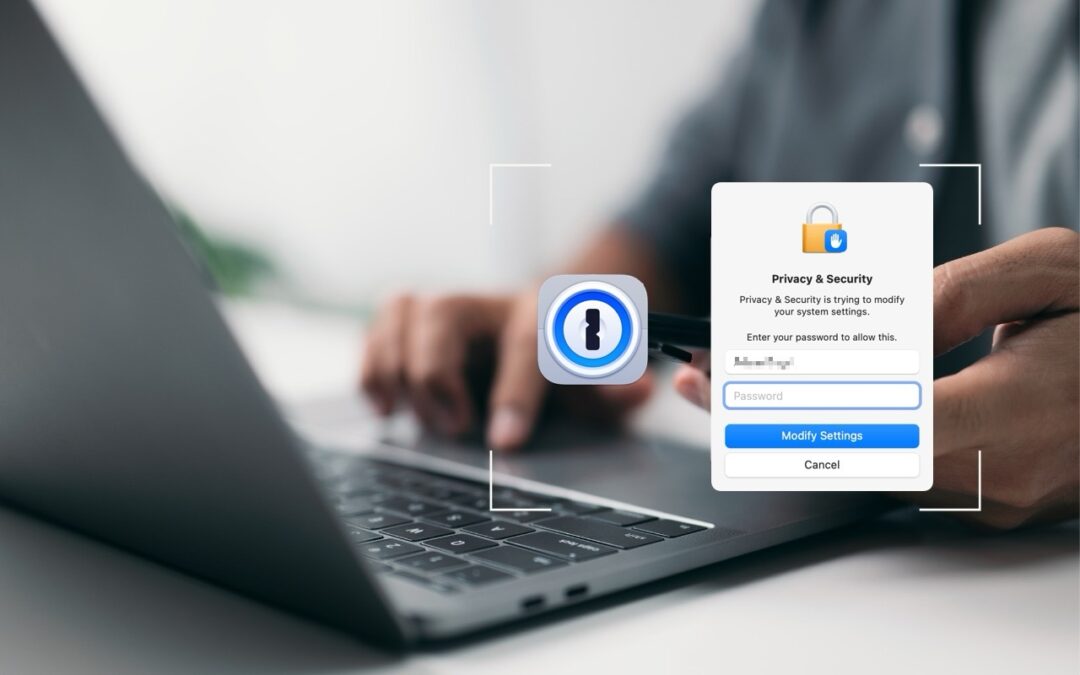
1Password is tremendously helpful for entering website passwords, but a little-known feature also enables it to enter your Mac login password for changing system settings, installing apps, and more.

Security experts no longer recommend password expiration policies that require users to change their passwords periodically. Here’s why.

In iOS 17.3, Apple has introduced Stolen Device Protection to discourage iPhone thefts enabled by a revealed passcode. It requires additional biometric authentication, and we recommend that everyone who uses Face ID or Touch ID enable it.
How to change the saving path of my screen recording?
Dosent filter anything
I have tried all of them and still unable to send pictures messages to android users. Help please
I wish I would have stayed with High Sierra or Catalina. Big Sur doesn't work with Time Machine, Messages, Spotlight…
My updated my Mac with Big Sur and it is stuck and says it has less than a minute to…